How to Create Admin User via Command Line in Magento 2
-
admin
-
December 19, 2025
-
Magento 2
-
0 Comments
Is is very simple to setup admin user with cli command. Please check cli command: User Name : admin Password : ILoveMagento2!123 php bin/magento admin:user:create –admin-user=admin –admin-password=ILoveMagento2!123 –admin-email=example@loveyou.com –admin-firstname=Zend –admin-lastname=Anwar
Continue Reading
How design a Jenkins setup for a large-scale enterprise application with multiple teams?
-
admin
-
January 16, 2025
-
DevOps
-
0 Comments
Design a master-agent architecture where the master handles scheduling and orchestrating jobs, and agents execute jobs. Use distributed builds by configuring Jenkins agents on different machines or containers. Implement folder-based multi-tenancy to isolate pipelines for each team. Secure the Jenkins setup using role-based access control (RBAC). Example: Team A has access to Folder A with restricted pipeline visibility, while the …
Continue Reading
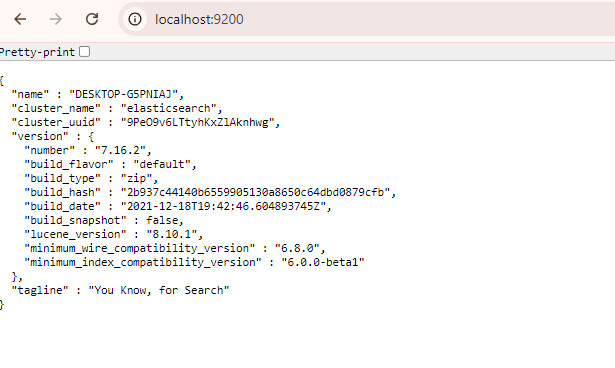
How to run Elasticsearch on localhost?
-
admin
-
September 8, 2024
-
DevOps, Magento 2
-
0 Comments
Please follow the following step: Download and install Elasticsearch Go to the bin directory (elasticsearch-7.16.2\bin) in the Elasticsearch installation folder Run the elasticsearch command Verify that Elasticsearch is running by going to the address in your web browser or by sending a GET request to localhost:9200
Continue Reading
How to install Jenkins?
-
admin
-
September 7, 2024
-
DevOps
-
0 Comments
Step 1: Install Java 1. Check if you already have Java installed on your Ubuntu system: # java -version 2. First, open a terminal window and update the system package repository by running: # sudo apt update 3. Depending on which Java version you want to install Java 11, run one of the following commands: # sudo apt-get install openjdk-11-jdk …
Continue Reading
What are the important features of Memcached?
-
admin
-
May 28, 2024
-
DevOps
-
0 Comments
Important features of Memcached includes CAS Tokens: A CAS token is attached to an object retrieved from a cache. You can use that token to save your updated object. Callbacks: It simplifies the code getDelayed: It reduces the delay time of your script which is waiting for results to come back from a server Binary protocol: You can use binary …
Continue Reading
What is Memcached?
-
admin
-
May 28, 2024
-
DevOps
-
0 Comments
Memcached is a free and open source, high-performance, distributed memory object caching system. The primary objective of Memcached is to enhance the response time for data that can otherwise be recovered or constructed from some other source or database. It is used to avoid the need to operate SQL database or another source repetitively to fetch data for a concurrent …
Continue Reading
What are the types of HTTP requests?
-
admin
-
May 28, 2024
-
DevOps
-
0 Comments
The types of Http requests are GET HEAD PUT POST PATCH DELETE TRACE CONNECT OPTIONS
Continue Reading
What are the popular tools for DevOps?
-
admin
-
May 28, 2024
-
DevOps
-
0 Comments
Some of the popular tools for DevOps are Jenkins Nagios Monit ELK (Elasticsearch, Logstash, Kibana) Jenkins Docker Ansible Git
Continue Reading
What is the key principle behind the DevOps?
-
admin
-
May 28, 2024
-
DevOps
-
0 Comments
The key aspects or principle behind DevOps is Infrastructure as code Continuous deployment Automation Monitoring Security
Continue Reading
What are the main components of a VPN?
-
admin
-
May 25, 2024
-
DevOps
-
0 Comments
Virtual Private Network (VPN) consists of folowing main components: Network Access Server (NAS): A NAS server is responsible for se ting up tunnels in a VPN that is accesses remotely. It maintains these tunnels that connect clients to VPN. Firewal : It is the software that creates barrier between VPN and public network. It protects the VPN from malicious activity …
Continue Reading